-
Security Products
Provide customers with advanced, innovative and effective cloud security products
-
About Us
Qingteng, Making the cloud more secure


Qingteng Sentry -Workload Adaptive Security Platform can automatically identify assets within the system and automatically correlate them with risk and intrusion events, providing flexible and efficient traceability.
Qingteng Sentry -Workload Adaptive Security Platform can proactively and accurately discover the security risks existing in the system and provide continuous risk monitoring and analysis capabilities.
Real-time detection of intrusion events, providing rapid defence and response capabilities.
CIS Benchmark requirements have been constructed to help users quickly conduct internal risks self-tests, identify security problems and repair them in a timely manner.
Combining multiple virus detection engines, Qingteng Sentry -Workload Adaptive Security Platform can accurately discover virus processes on the workload in real time and provide multi-angle analysis results as well as corresponding virus processing capabilities.
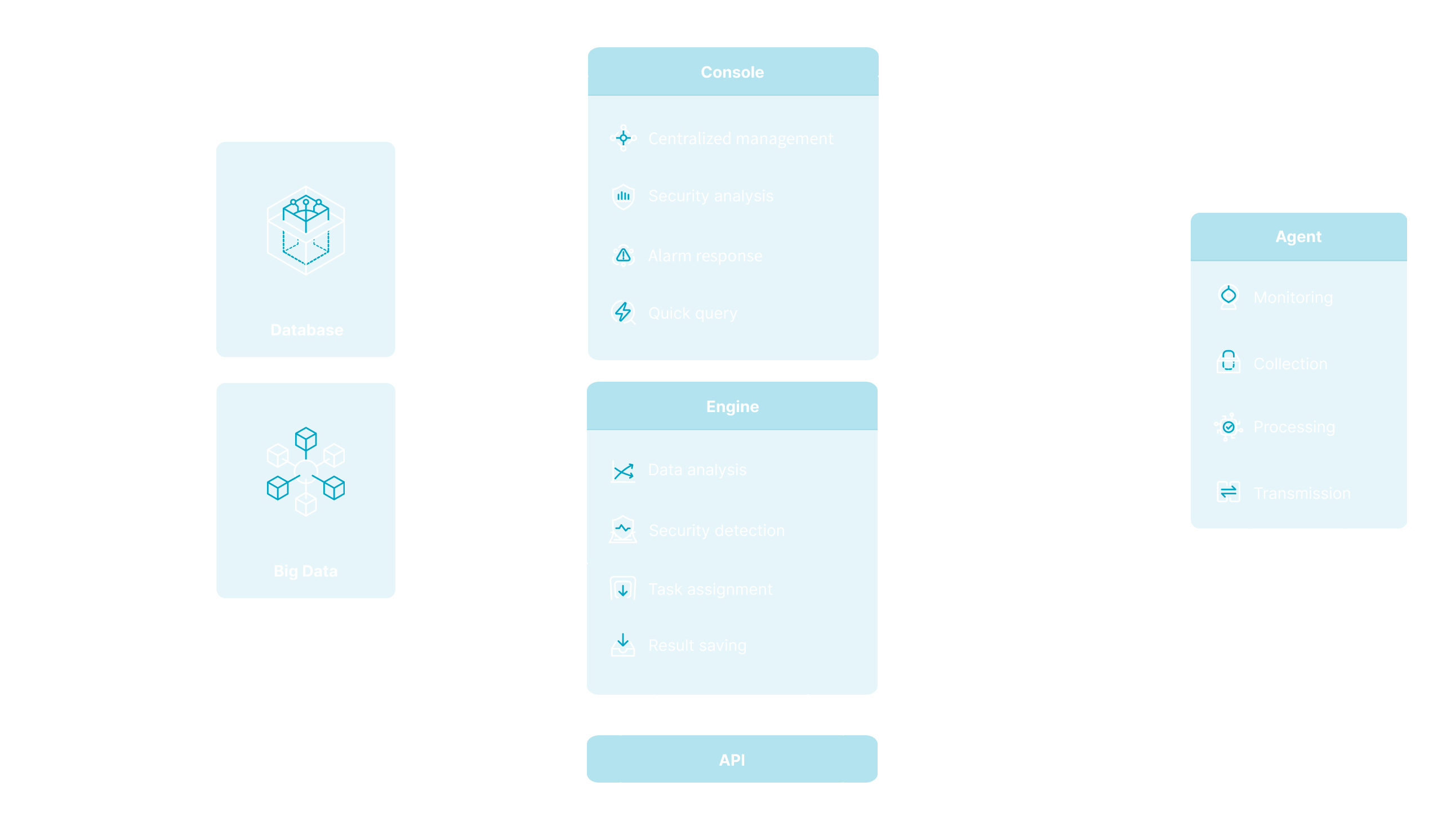
The Agent can be installed on the workloads with only one single command, and automatically adapts to various physical machines, virtual machines and cloud environments. It runs stably and with low consumption, and can continuously collect host processes, ports and account information, and monitor workloads process, network connections and other behaviours in real time. In addition, The Agent also can communicate with the Server-side to perform the tasks it issued and proactively find workloads Security problems.
Server, as the information processing hub of the core platform, supports horizontal scaling and distributed deployment, can continuously analyse and detect the information and behaviours received from each Agent and save them. It can find security risks, such as vulnerabilities, weak passwords, etc., and anomalous behaviours, such as Webshell writing behaviours, abnormal login behaviours, abnormal network connection behaviours, abnormal command invocation, etc., from various dimensions of information, thus achieving real-time early warning of intrusion behaviours.
Interact with users in the form of a Web console, clearly display the results of security monitoring and analysis, and provide real-time alerts on major threats to help users slove security problems better and faster, and provide centralised management of security tools to facilitate the user's system configuration and management, security response and other related operations.


Shelling protection for Agent to prevent tampering; using encrypted transmission to communicate with the server-side to ensure data security.


With 8,000,000+ servers running practice, the stability up to 99.9999%; Agent 2-minutes offline automatic reboot mechanism to ensure that the system is always being monitored.


Under normal system load, CPU usage is less than 1%, and memory usage is less than 40M, resulting in extremely low consumption. When the system load is too high, the Agent is actively downgraded to strictly limit the consumption of system resources and ensure the normal operation of the business system.

Named to Gartner's Cloud Workload Protection Platform Market Guide(CWPP) for the seventh consecutive year
IDC CWPP Market Share Report: China Private Cloud Cloud Workload Security Market Share, 2022: Compliance as Roots, Technology as Backbone
Frost&Sullivan's China Cloud Hosting Security Market Report 2022, Ranked No. 1 in Overall Competitiveness