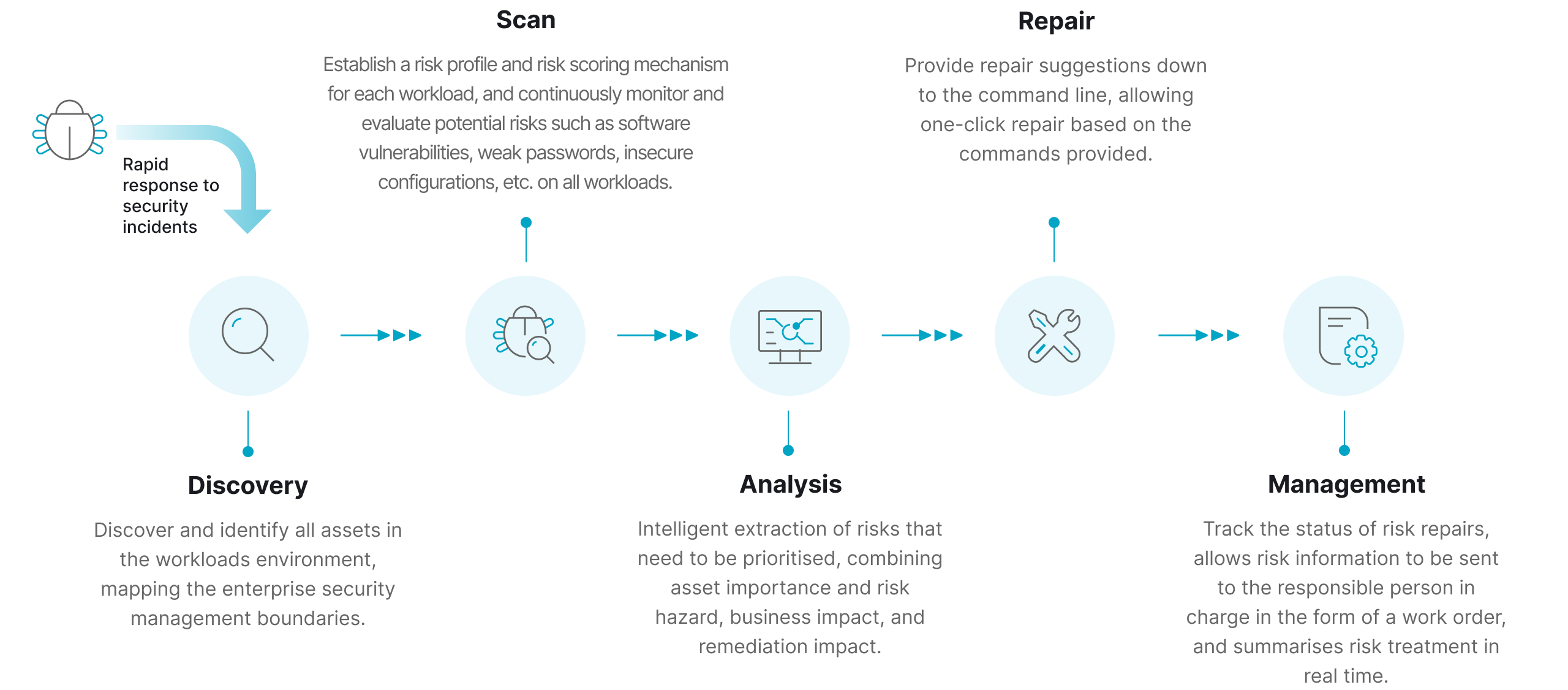
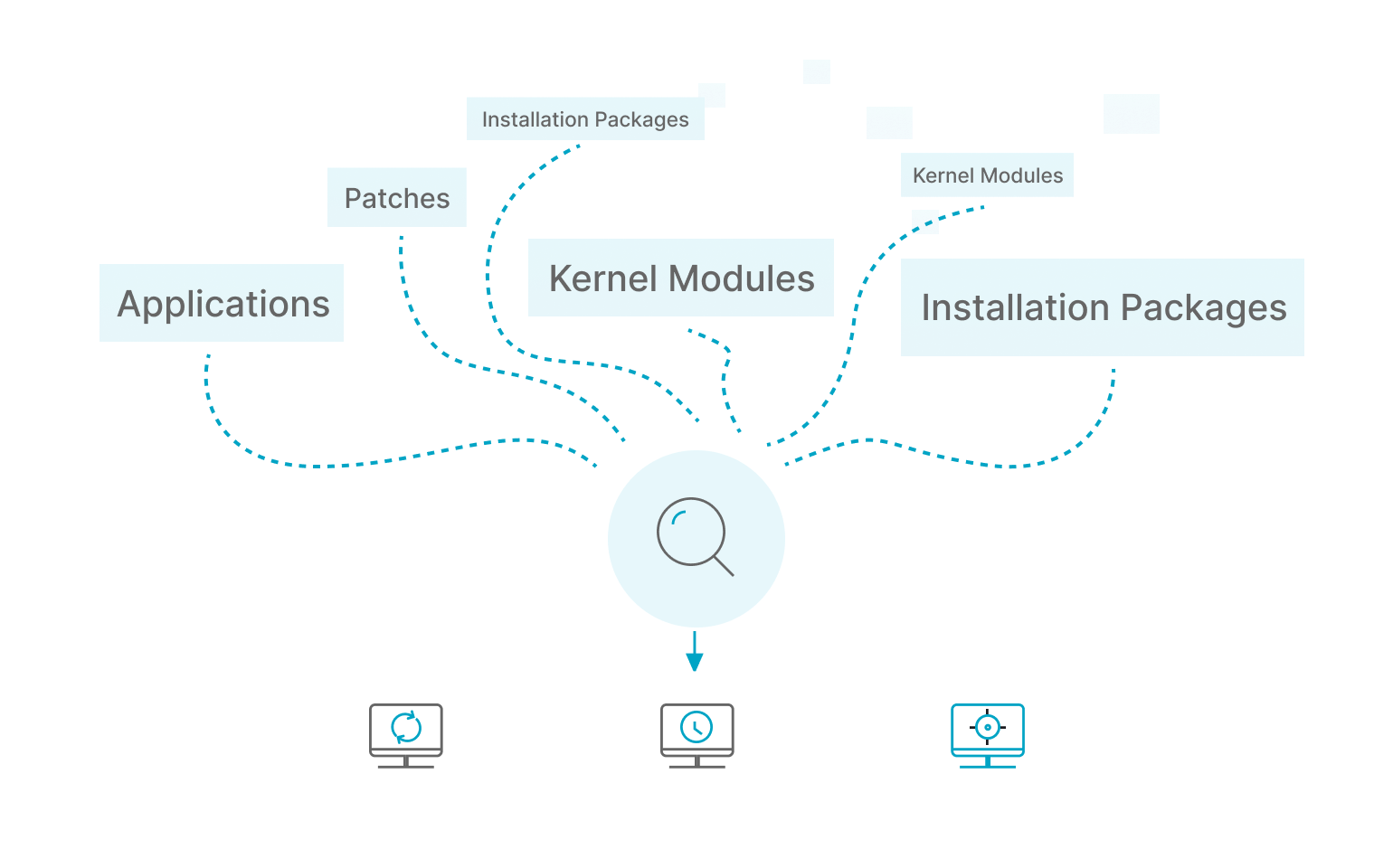
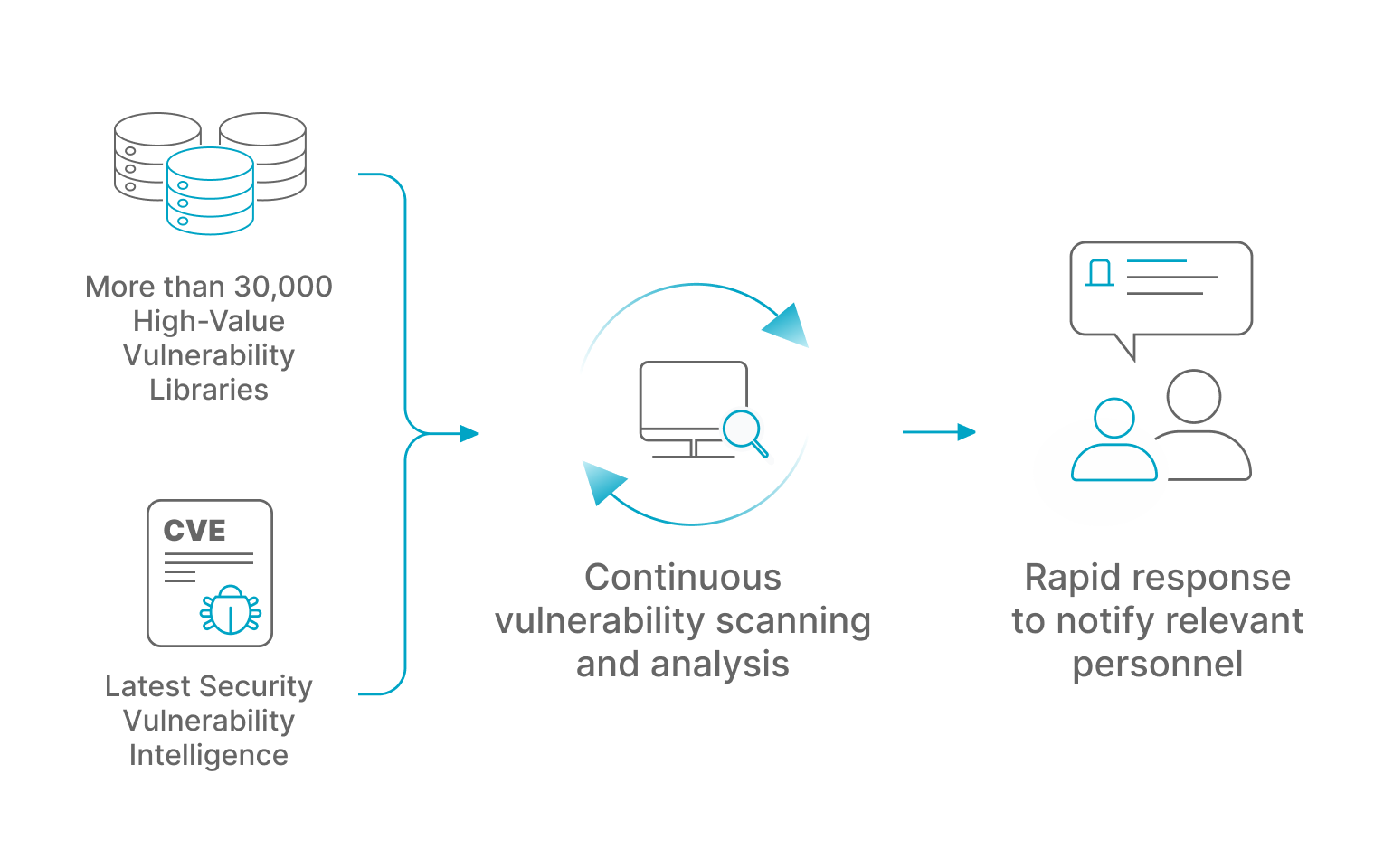
Discover uninstalled
critical patches
Continuously updated patch library and agent probe scanning can timely and accurately find important patches that need to be applied to the system. At the same time, in-depth detection of applications, kernel modules, installation packages, etc., all kinds of important software updates in the system, intelligent extraction of urgently needed patches.