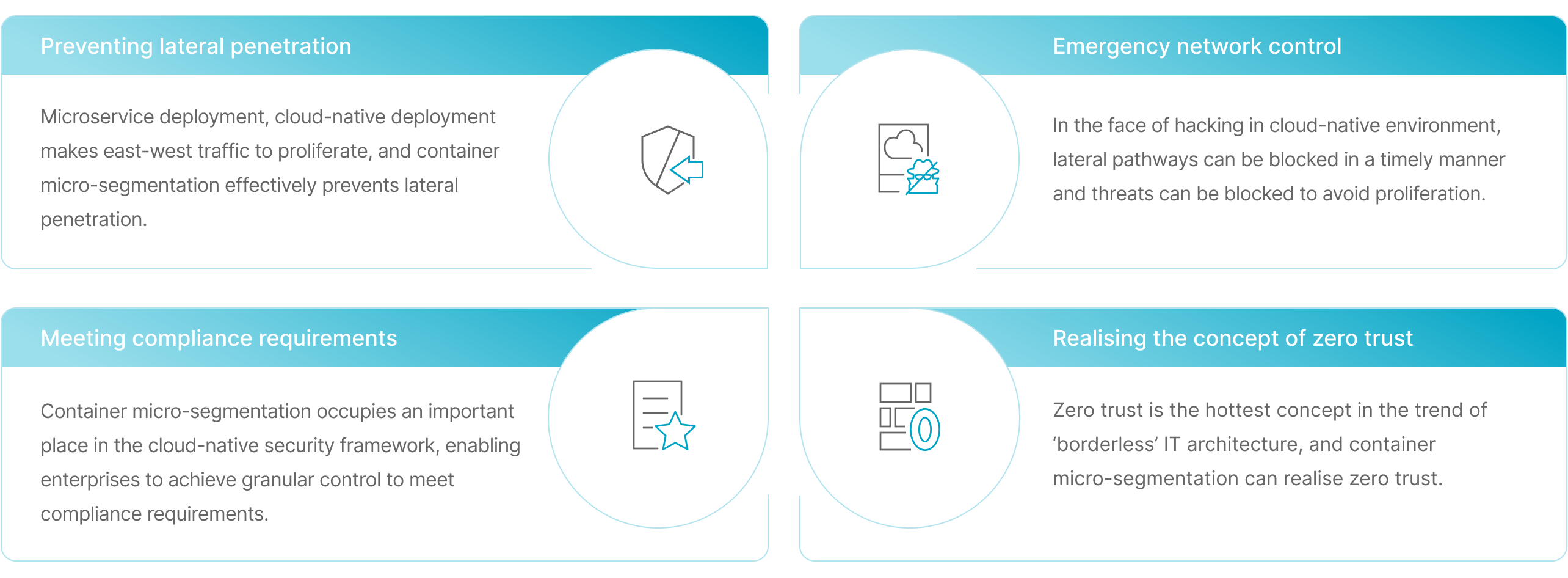
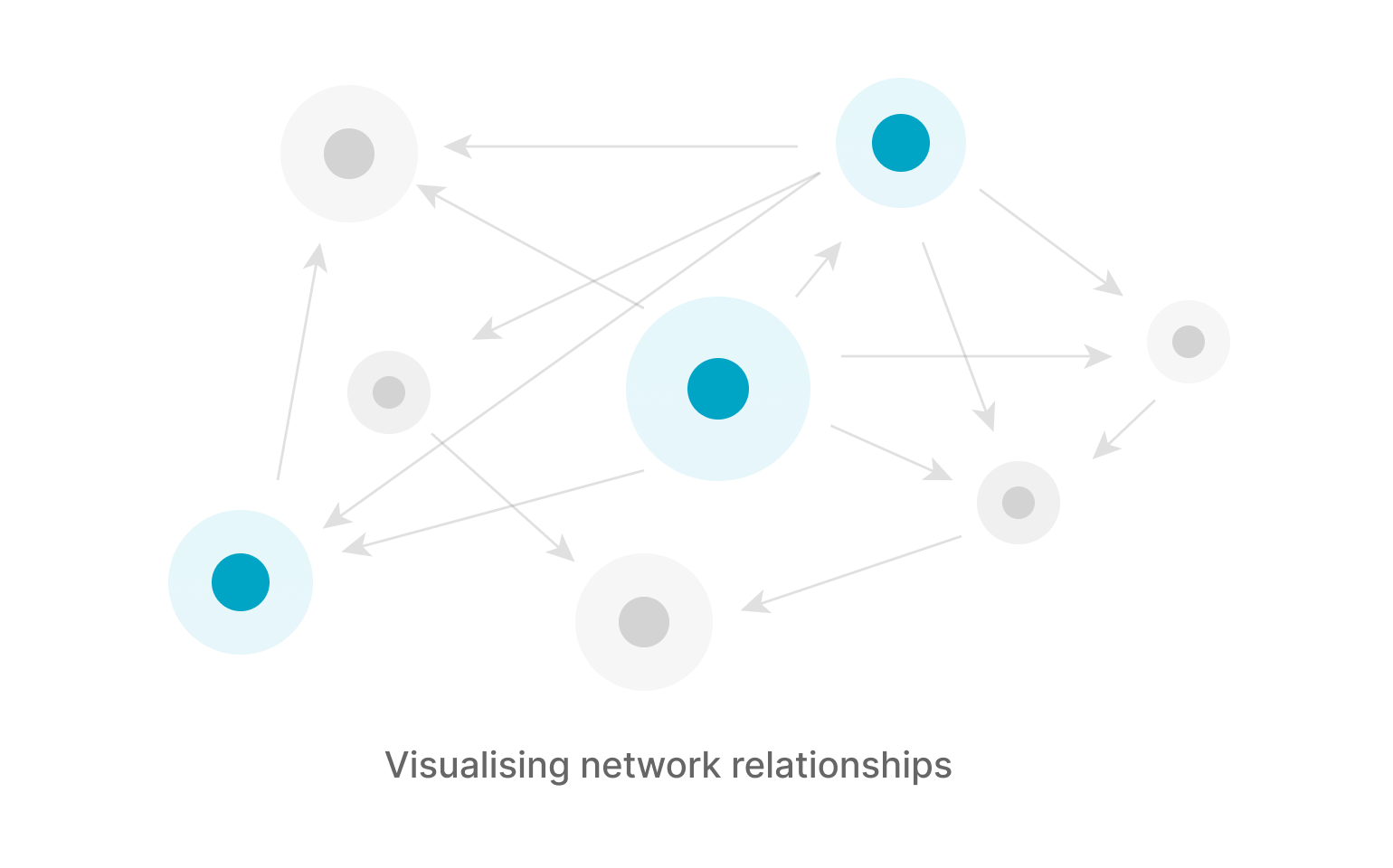
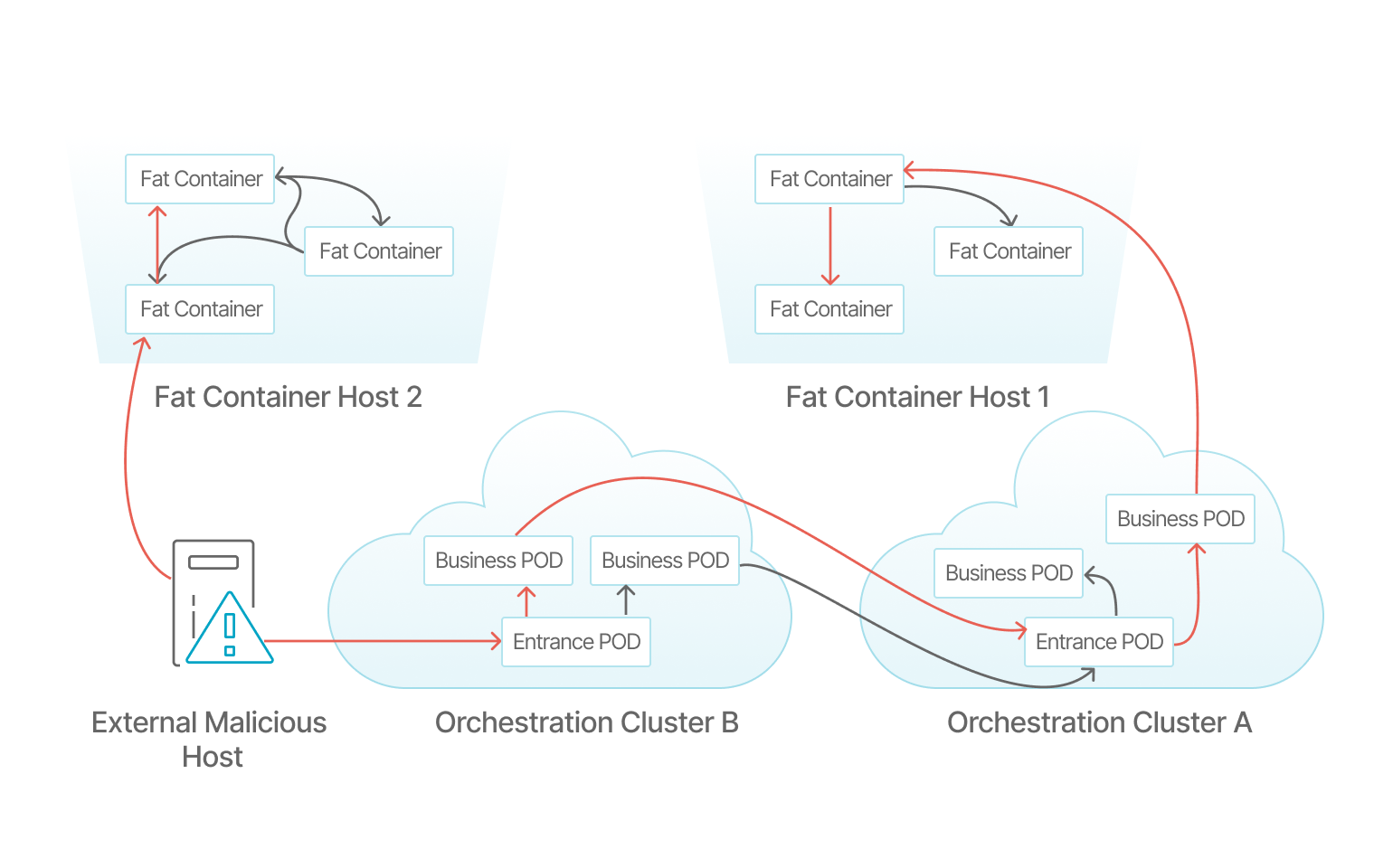
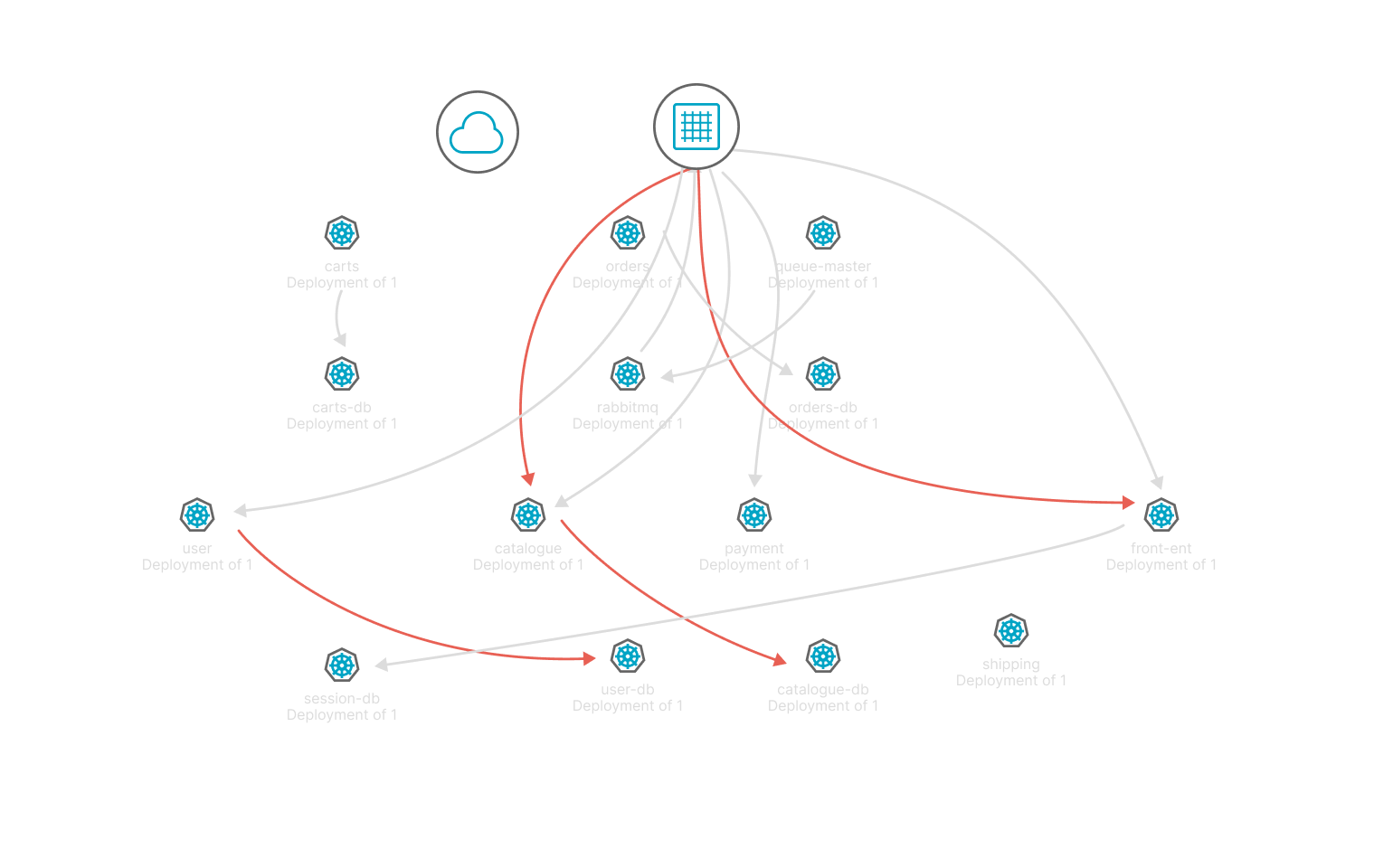
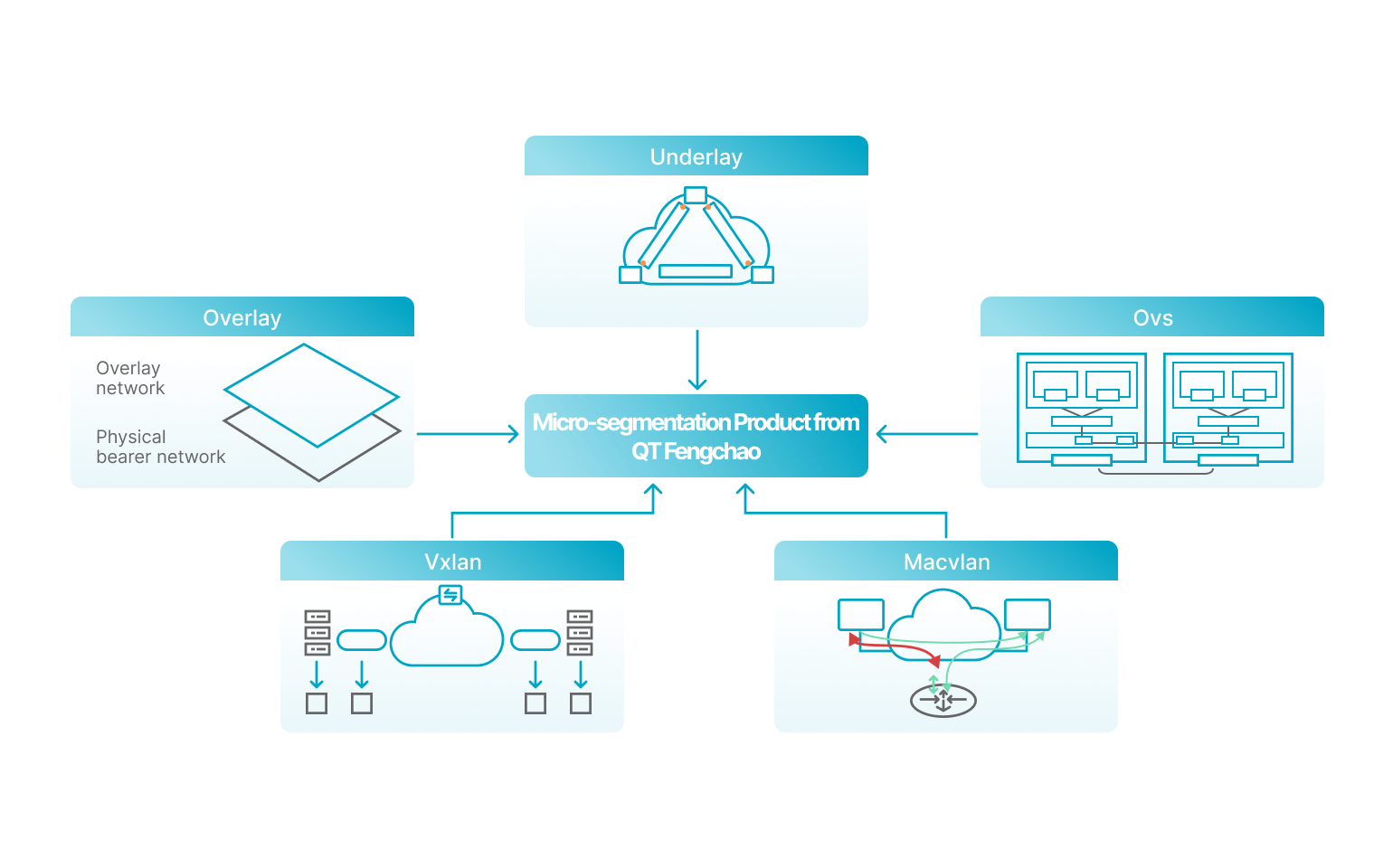
Provide network topology relationship from business perspective
Based on the actual business workload visual display of the access behaviour between containers, clearly show the network topology relationship, convenient for operation and security personnel to understand.