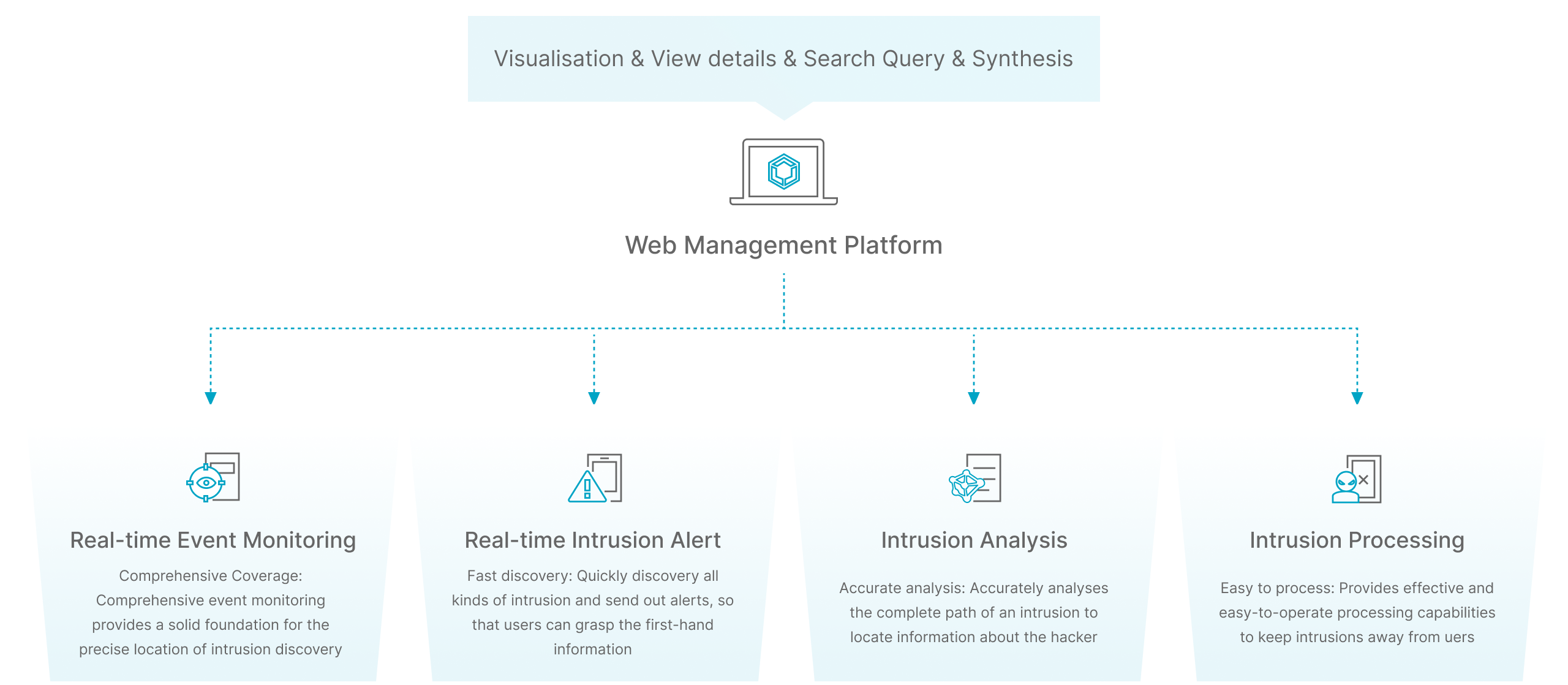
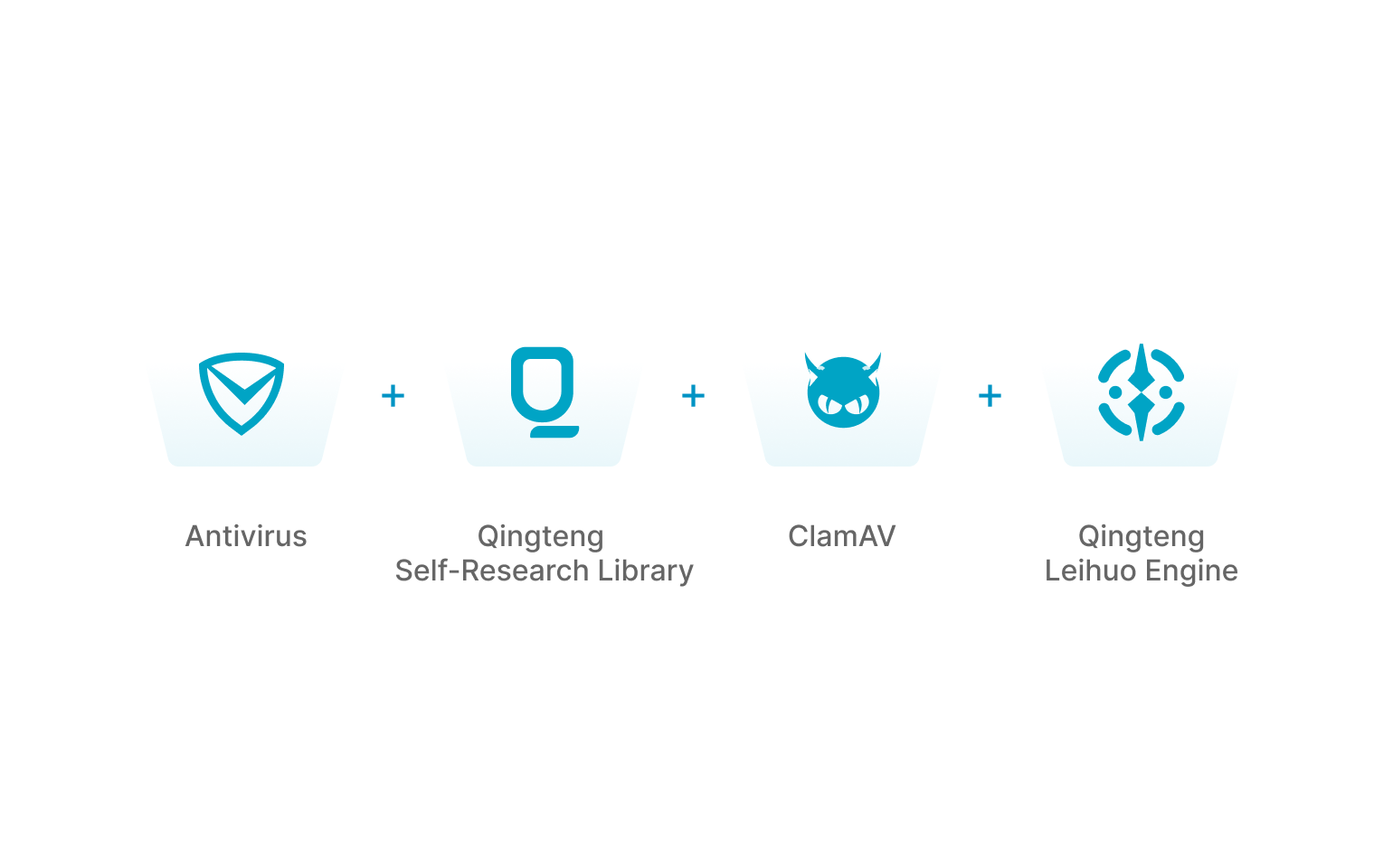
Detection based on known threats
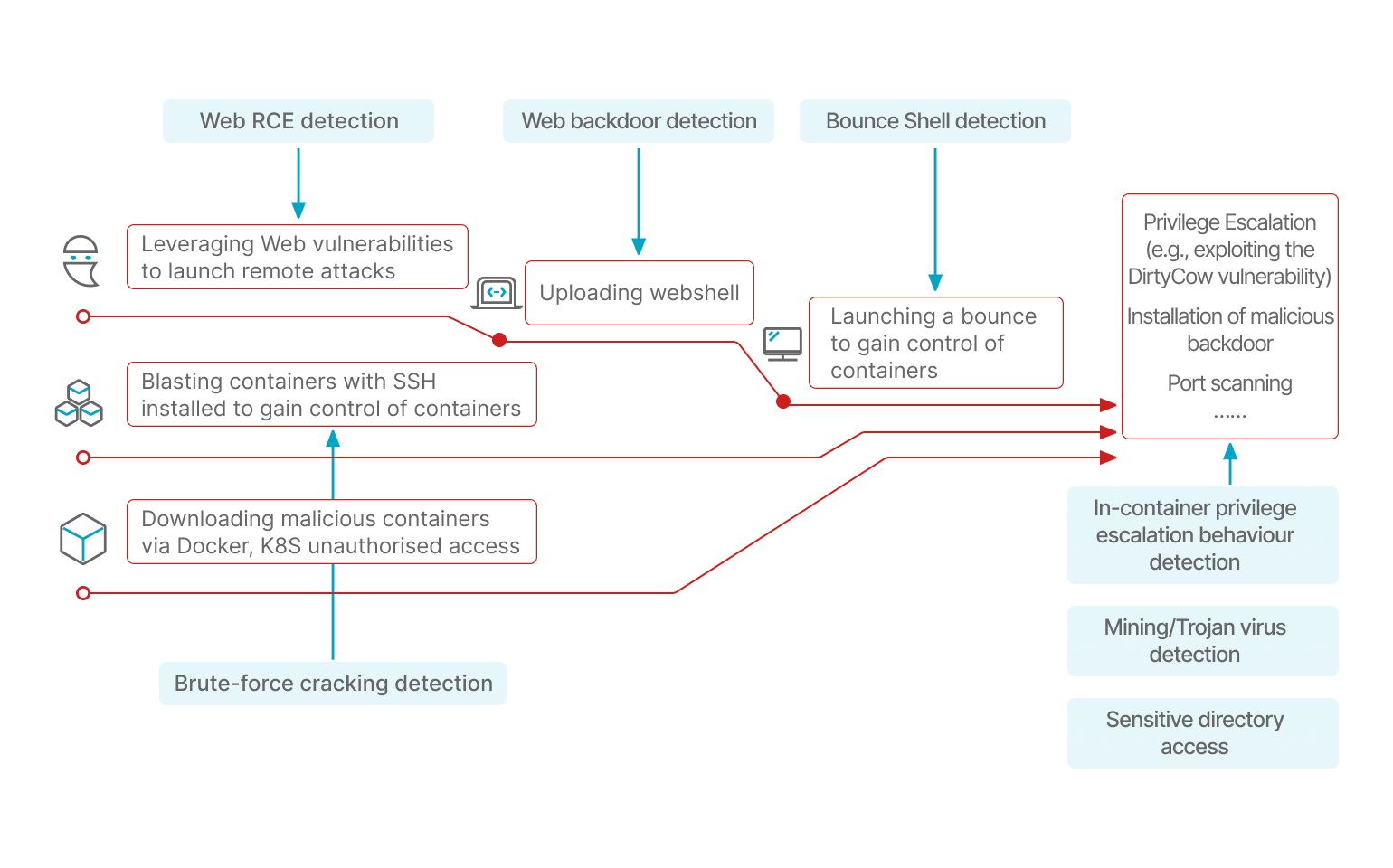
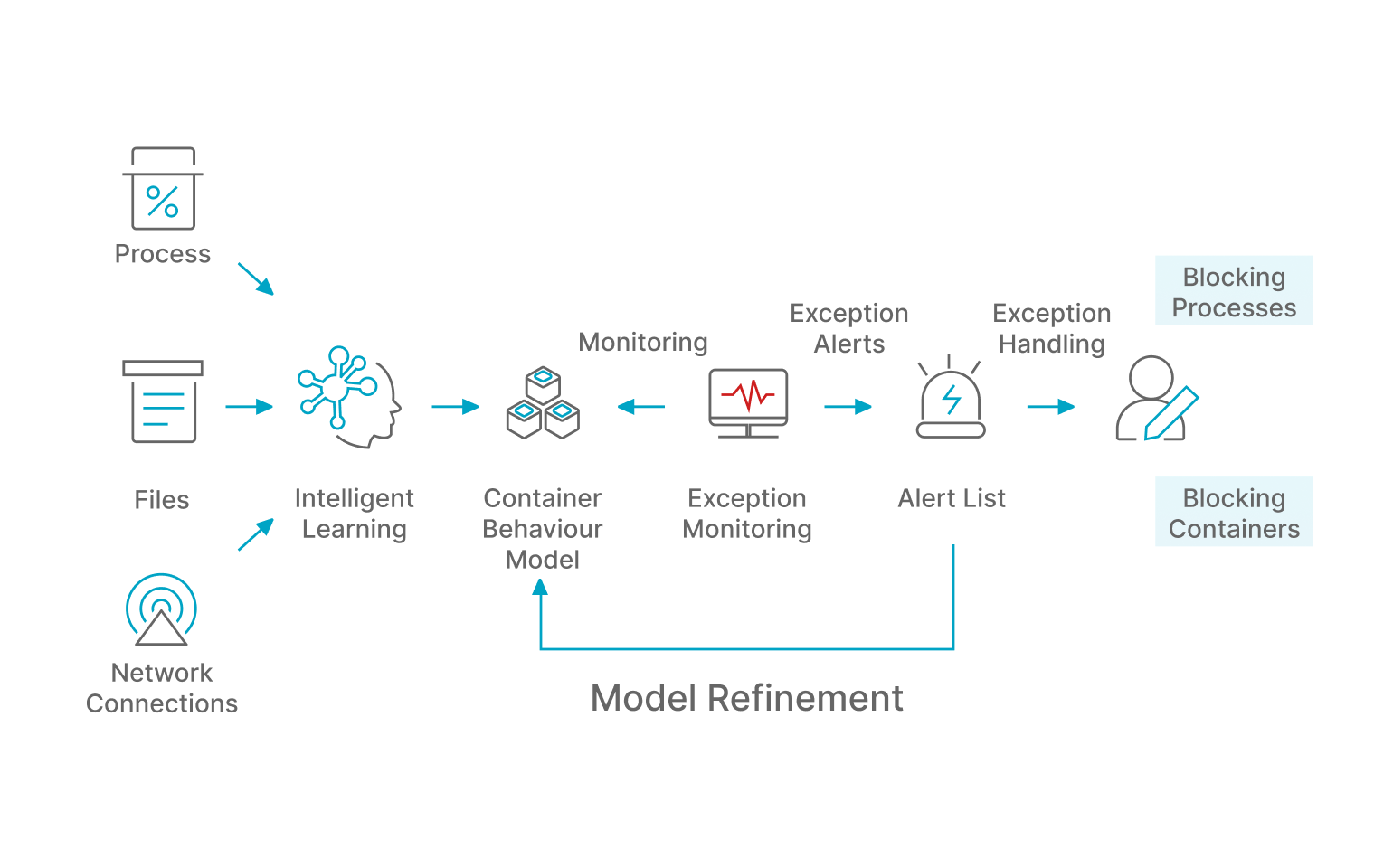
By monitoring process creation, file changes and other behaviours within containers, Qingteng Sentry -Cloud Native Security Platform obtains behavioural characteristics, which are then examined by Qingteng's detection engines in order to detect viruses, mining, Webshell and other attacks in containers.