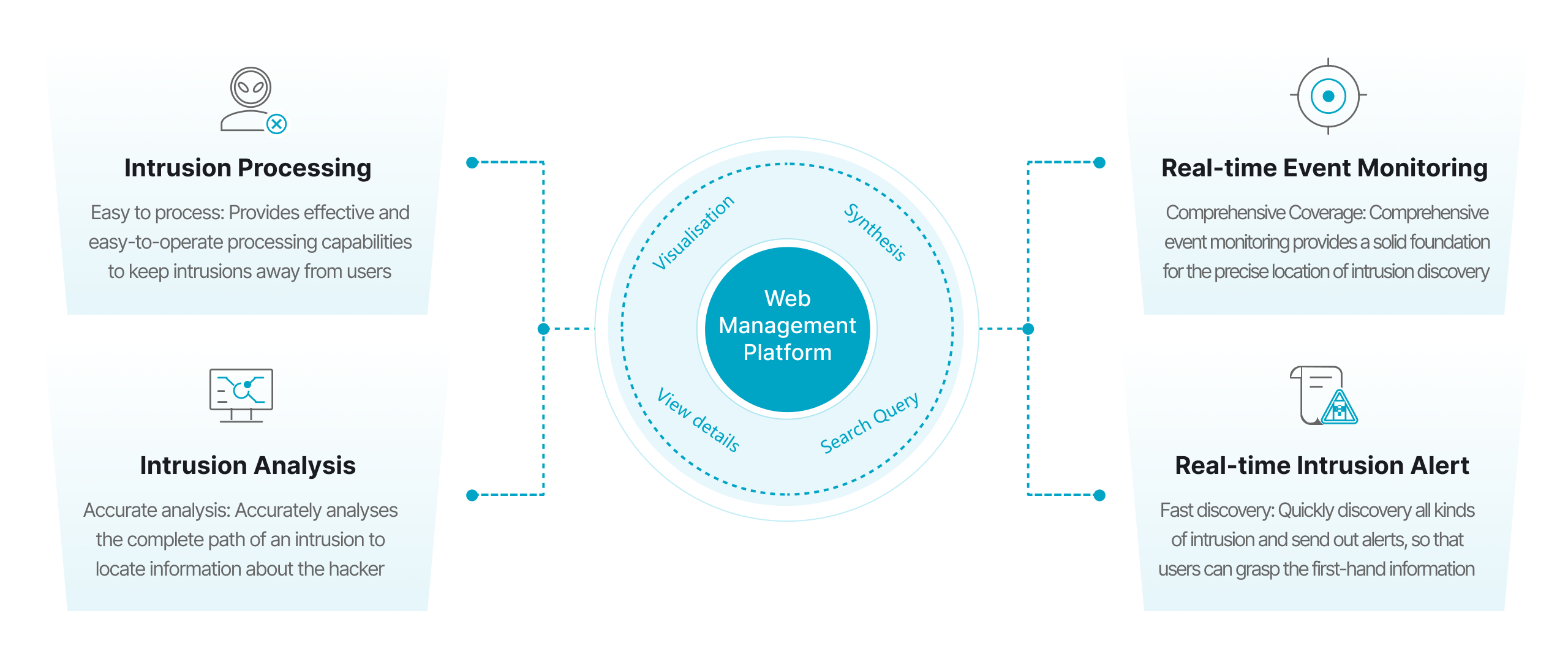
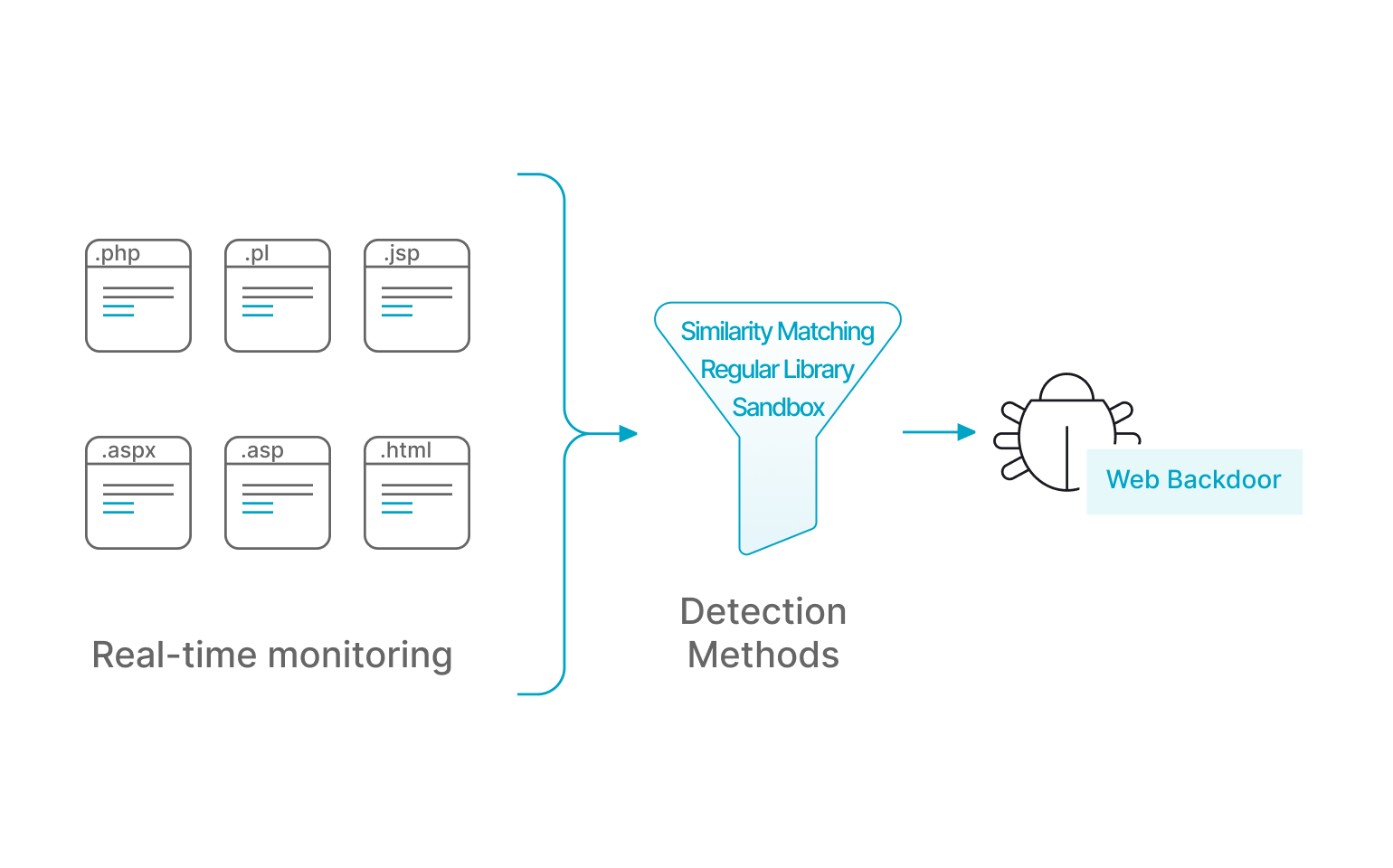
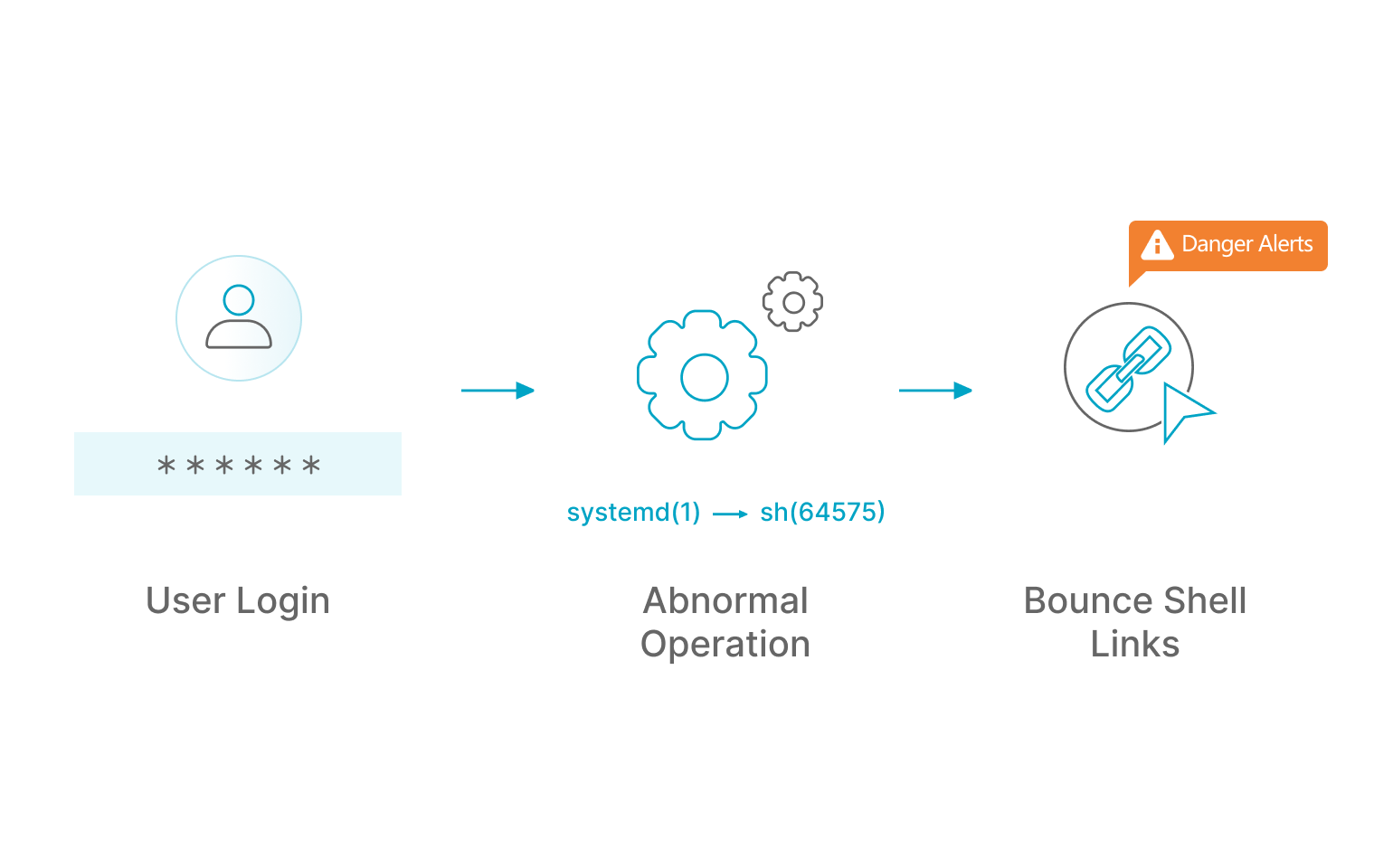
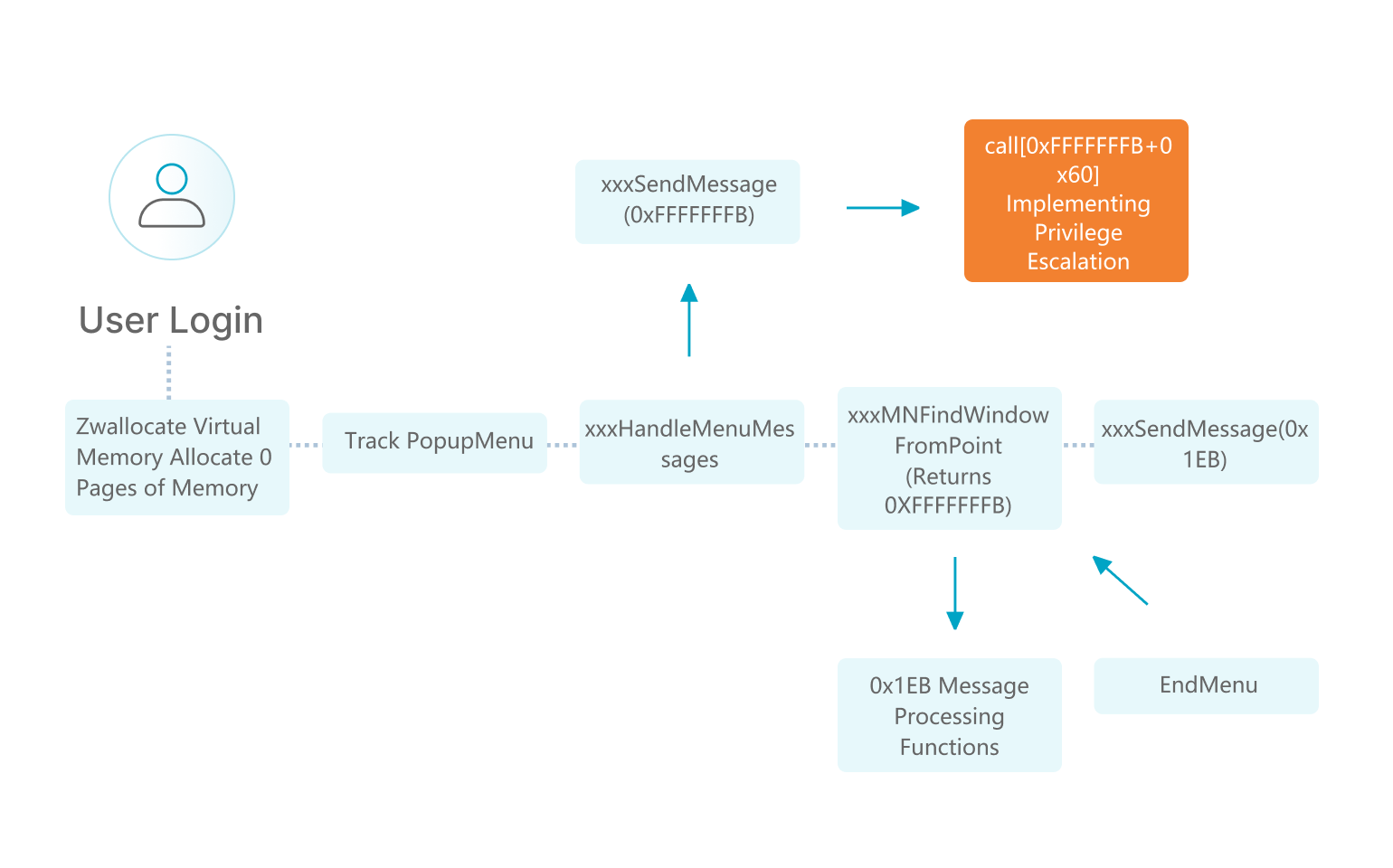
Web Backdoor
Detection
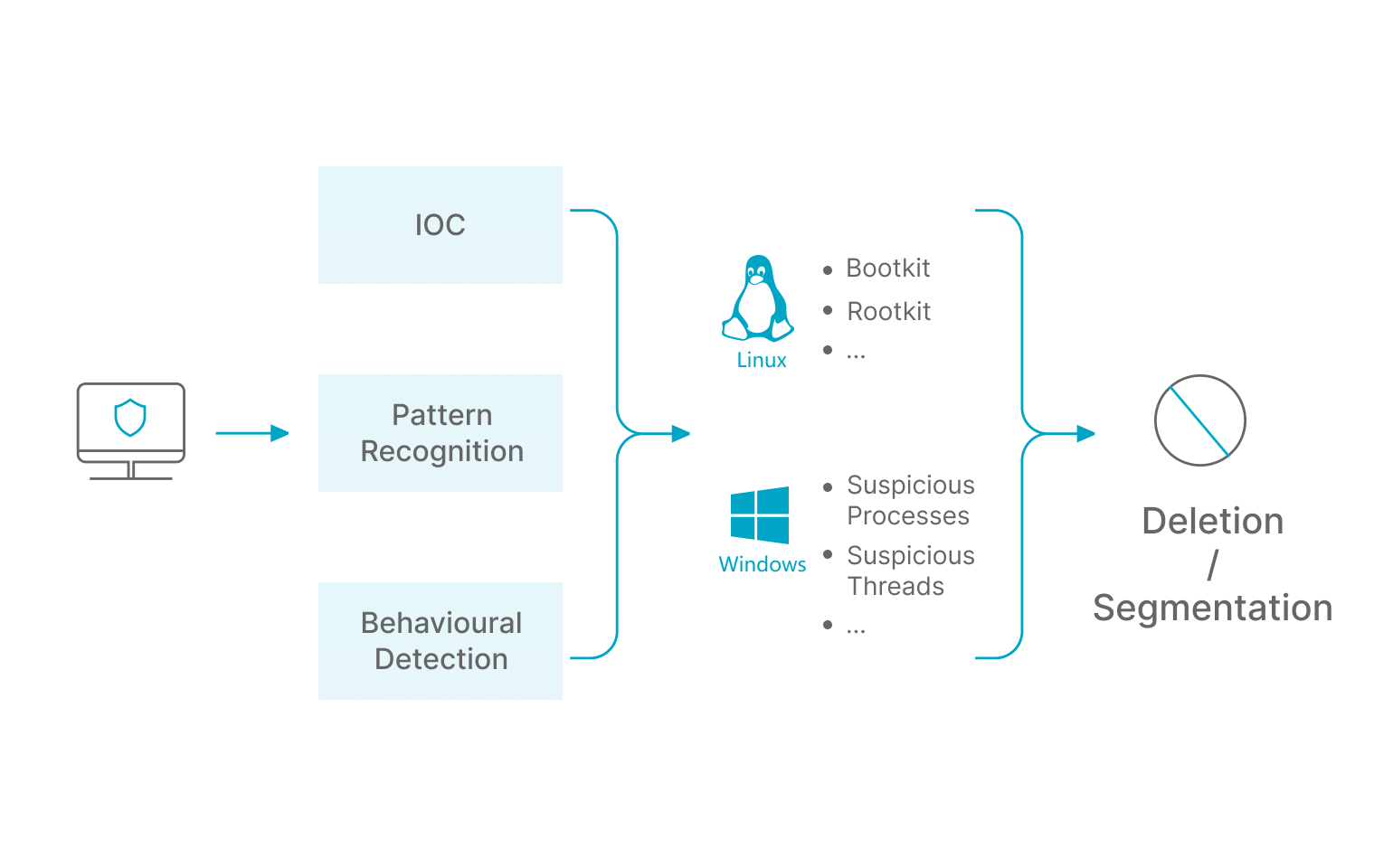
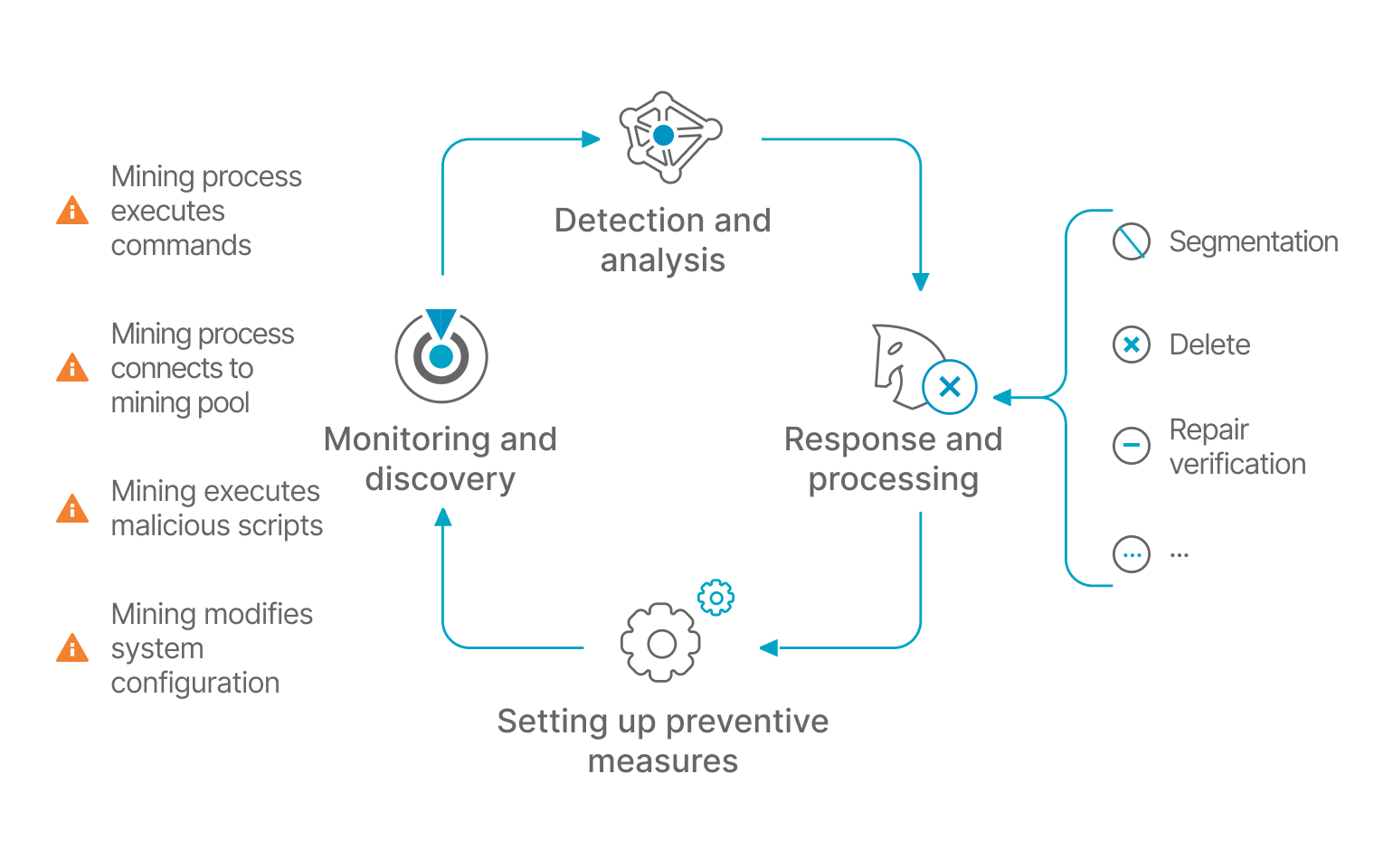
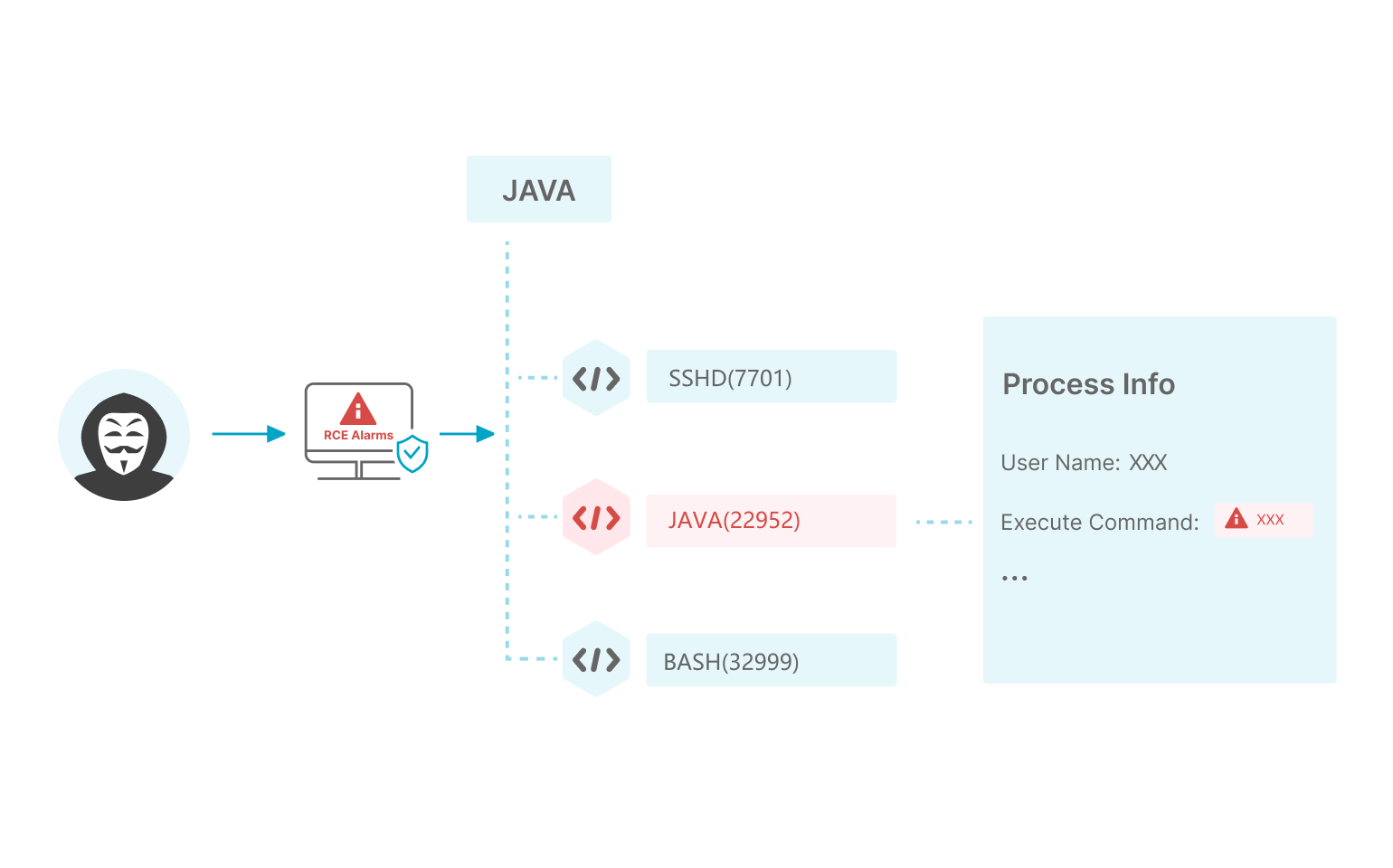
By automating the monitoring of critical paths, combining regular libraries, similarity matching, sandboxing and other detection methods, real-time file change detection, so that web backdoors can be detected in a timely manner and the affected part of the backdoor can be clearly labelled.